THE CHALLENGE
In IP data communication networks, router and switches may create a tunnel between two points on a network that can securely transmit any kind of data between them. Tunnelling involves the encapsulation of an IP packet within another packet, adding a packet header. This encapsulation enables the packet to reach its destination through intermediary networks that do not support the packet’s protocol.
Different type of header may be used, depending on the place in the network and / or on the type of the network. A few examples are GRE, VLAN, MPLS, VN-Tag, VXLAN and GTP-U headers.
One example in telecommunication networks is GTP-U tunnel: it is used for efficiently carrying large volumes of user data within the mobile core network and between the radio access network and the core network.
In IP networks, one key application for MPLS tunnelling is switching traffic for a large enterprise across the service provider backbone, where MPLS labels keep the traffic distinct from other enterprises. In this case we may be in the following condition, when tapping MPLS tunnels between two routers, where they may be also the case that multiple stacked tags or labels might be present:
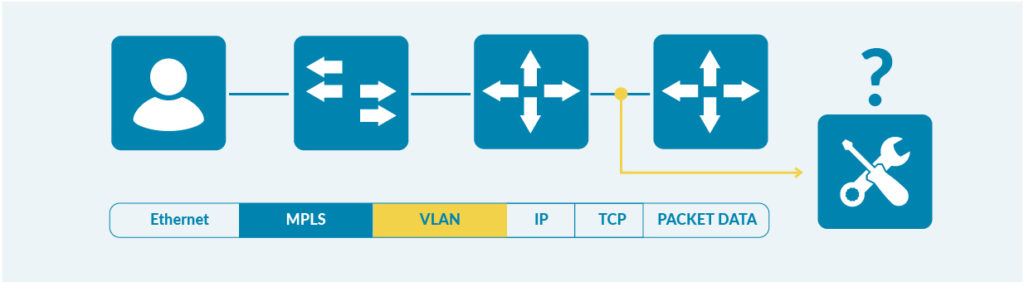
Tools that are not MPLS–aware nor VLAN-aware will not be able to analyse traffic received
The problem is that monitoring tools do usually not recognize tunnel headers, and the consequence is that they discard these packets as wrong packets, making impossible to properly analyse such networks.
Header stripping is a useful feature also if the monitoring tools are able to recognize the tunnels and do the stripping, because doing that in an external appliance may provide greater efficiency for the tool where this process would degrade performances.
WHAT WE DO
Microtel Innovation NPB and Visibility Appliances analyses the input traffic, identifies specific headers such as MPLS, VLAN, VXLAN, VN-TAG, GTP-U and GRE, and removes them before sending the packets to the appropriate security and analysis tools.
In this way analysis and monitoring tools are able to process traffic flows that they otherwise could not recognize because of an unreadable header type.
The solution is highly performant and scalable. Moreover, Microtel Innovation header stripping restores the inner frames: after this manipulation the resulting frame is a valid IP packet with a correct checksum.
Here is an example on how our system works:
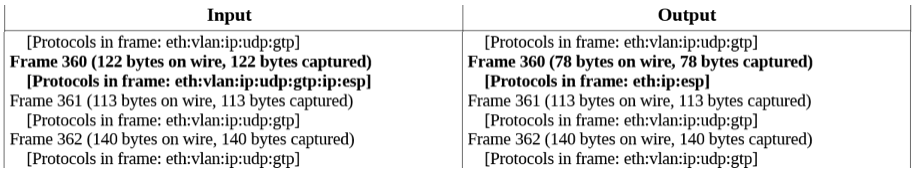
- In Fig1 GTP-U header stripping is enabled, using the NPB GUI
- Fig2 shows the result of the operation on the output traffic: since only frame 360 is GTP-U, this is the only one de-tunneled by the device.
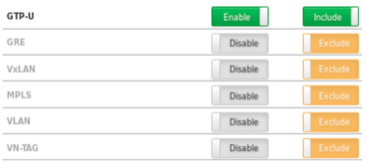
Fig1: GTP-U header stripping is configured in the NPB GUI